はじめに
掲題の通り、CCNPの学習を深めるために検証した際の記録です。
IPsecやGREトンネルの説明は調べるとよくでてくるので、説明は割愛します。
検証
構成図
基本的な構成は下記です。RT01とRT04でGREトンネルとIPsecで接続しています。
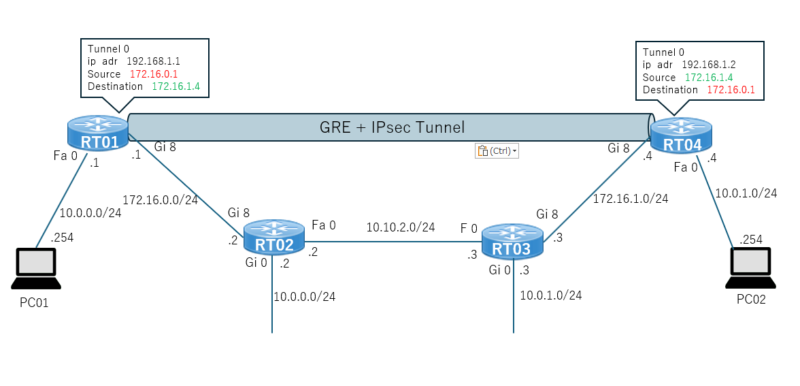
通信の中を確認したいので、RT02とRT03の間にL2SWを接続し、RT02とRT03間の通信をパケットキャプチャします。
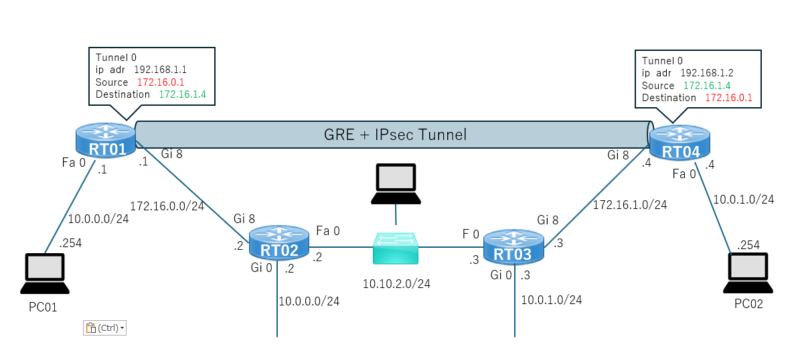
IPsecの設定有無で見え方の違いも確認してみます。
設定
※管理用(ログイン用)にVLAN99を作成しています。VLAN99はIPsecの設定には関係はありません。
流し込みconfig
以下、検証設定のために実行コマンドです。
RT01
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
conf t crypto isakmp policy 1 encry 3des hash md5 authentication pre-share group 2 crypto isakmp key orange address 172.16.1.4 crypto isakmp keepalive 10 periodic crypto ipsec transform-set ORANGE-IPSEC esp-3des esp-md5-hmac mode transport ip access-list extended Allow-ipsec-p2p permit gre host 172.16.0.1 host 172.16.1.4 crypto map Cryoto-ipsec-map 1 ipsec-isakmp set peer 172.16.1.4 set transform-set ORANGE-IPSEC match address Allow-ipsec-p2p interface FastEthernet0 ip address 10.0.0.1 255.255.255.0 ip tcp adjust-mss 1332 no shutdown interface GigabitEthernet 8 ip address 172.16.0.1 255.255.255.0 no shutdown crypto map Cryoto-ipsec-map interface Tunnel 0 ip address 192.168.1.1 255.255.255.0 ip mtu 1372 tunnel source GigabitEthernet8 tunnel destination 172.16.1.4 ip route 0.0.0.0 0.0.0.0 Tunnel0 ip route 172.16.1.4 255.255.255.255 172.16.0.2 end wr |
RT02
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
conf t vlan 10 exit interface vlan 10 ip address 10.0.0.2 255.255.255.0 interface GigabitEthernet0 switchport access vlan 10 exit interface FastEthernet0 ip address 10.10.2.2 255.255.255.0 no shutdown interface GigabitEthernet 8 ip address 172.16.0.2 255.255.255.0 no shutdown ip route 172.16.1.0 255.255.255.0 10.10.2.3 end wr |
RT03
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
conf t vlan 10 exit interface vlan 10 ip address 10.0.1.3 255.255.255.0 interface GigabitEthernet0 switchport access vlan 10 exit interface FastEthernet0 ip address 10.10.2.3 255.255.255.0 no shutdown interface GigabitEthernet 8 ip address 172.16.1.3 255.255.255.0 no shutdown ip route 172.16.0.0 255.255.255.0 10.10.2.2 end wr |
RT04
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
conf t crypto isakmp policy 1 encry 3des hash md5 authentication pre-share group 2 crypto isakmp key orange address 172.16.0.1 crypto isakmp keepalive 10 periodic crypto ipsec transform-set ORANGE-IPSEC esp-3des esp-md5-hmac mode transport ip access-list extended Allow-ipsec-p2p permit gre host 172.16.1.4 host 172.16.0.1 crypto map Cryoto-ipsec-map 1 ipsec-isakmp set peer 172.16.0.1 set transform-set ORANGE-IPSEC match address Allow-ipsec-p2p interface FastEthernet0 ip address 10.0.1.4 255.255.255.0 ip tcp adjust-mss 1332 no shutdown interface GigabitEthernet 8 ip address 172.16.1.4 255.255.255.0 no shutdown crypto map Cryoto-ipsec-map interface Tunnel 0 ip address 192.168.1.2 255.255.255.0 ip mtu 1372 tunnel source GigabitEthernet8 tunnel destination 172.16.0.1 ip route 0.0.0.0 0.0.0.0 Tunnel0 ip route 172.16.0.1 255.255.255.255 172.16.1.3 end wr |
sh run
検証に使用したconfigを載せます。
RT01# sh run
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 |
RT01#sh run Building configuration... Current configuration : 2680 bytes ! ! Last configuration change at 04:48:45 UTC Tue Jan 28 2025 by admin ! version 15.4 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname RT01 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$WJFk$6QRnNnLWC.ajxzqfzkYi4/ ! no aaa new-model memory-size iomem 15 ! ! ! ! ! ! ! ! ! ! ! ! ! ! no ip domain lookup ip domain name orange.local ip cef no ipv6 cef ! ! ! ! ! multilink bundle-name authenticated ! ! ! ! ! ! ! ! cts logging verbose license udi pid C891FJ-K9 sn FGL2505LDK2 ! ! vtp mode transparent username admin password 7 1218011A1B05 ! ! ! ! ! vlan 99 ! ip ssh version 2 ! ! crypto isakmp policy 1 encr 3des hash md5 authentication pre-share group 2 crypto isakmp key orange address 172.16.1.4 crypto isakmp keepalive 10 periodic ! ! crypto ipsec transform-set ORANGE-IPSEC esp-3des esp-md5-hmac mode transport ! ! ! crypto map Cryoto-ipsec-map 1 ipsec-isakmp set peer 172.16.1.4 set transform-set ORANGE-IPSEC match address Allow-ipsec-p2p ! ! ! ! ! ! interface Tunnel0 ip address 192.168.1.1 255.255.255.0 ip mtu 1372 tunnel source GigabitEthernet8 tunnel destination 172.16.1.4 ! interface BRI0 no ip address encapsulation hdlc shutdown isdn termination multidrop ! interface FastEthernet0 ip address 10.0.0.1 255.255.255.0 ip tcp adjust-mss 1332 duplex auto speed auto ! interface GigabitEthernet0 no ip address ! interface GigabitEthernet1 no ip address ! interface GigabitEthernet2 no ip address ! interface GigabitEthernet3 no ip address ! interface GigabitEthernet4 no ip address ! interface GigabitEthernet5 no ip address ! interface GigabitEthernet6 no ip address ! interface GigabitEthernet7 switchport access vlan 99 no ip address ! interface GigabitEthernet8 ip address 172.16.0.1 255.255.255.0 duplex auto speed auto crypto map Cryoto-ipsec-map ! interface Vlan1 no ip address ! interface Vlan99 ip address 192.168.99.3 255.255.255.0 ! interface Async3 no ip address encapsulation slip ! ip forward-protocol nd no ip http server no ip http secure-server ! ! ip route 0.0.0.0 0.0.0.0 Tunnel0 ip route 172.16.1.4 255.255.255.255 172.16.0.2 ! ip access-list extended Allow-ipsec-p2p permit gre host 172.16.0.1 host 172.16.1.4 ! ! ! control-plane ! ! mgcp behavior rsip-range tgcp-only mgcp behavior comedia-role none mgcp behavior comedia-check-media-src disable mgcp behavior comedia-sdp-force disable ! mgcp profile default ! ! ! ! ! ! ! line con 0 login local no modem enable line aux 0 line 3 modem InOut speed 115200 flowcontrol hardware line vty 0 4 login local transport input all ! scheduler allocate 20000 1000 ! ! ! end |
RT02# sh run
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 |
RT02#sh run Building configuration... Current configuration : 2080 bytes ! ! Last configuration change at 01:04:12 UTC Tue Jan 28 2025 by admin ! version 15.4 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname RT02 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$Vkhk$mzfGeEt/yBY7LMijPoV21/ ! no aaa new-model memory-size iomem 15 ! ! ! ! ! ! ! ! ! ! ! ! ! ! no ip domain lookup ip domain name orange.local ip cef no ipv6 cef ! ! ! ! ! multilink bundle-name authenticated ! ! ! ! ! ! ! ! cts logging verbose license udi pid C891FJ-K9 sn FGL2505LDK4 ! ! vtp mode transparent username admin password 7 070E25414707 ! ! ! ! ! vlan 10,99 ! ip ssh version 2 ! ! ! ! ! ! ! ! ! ! ! interface BRI0 no ip address encapsulation hdlc shutdown isdn termination multidrop ! interface FastEthernet0 ip address 10.10.2.2 255.255.255.0 duplex auto speed auto ! interface GigabitEthernet0 switchport access vlan 10 no ip address ! interface GigabitEthernet1 no ip address ! interface GigabitEthernet2 no ip address ! interface GigabitEthernet3 no ip address ! interface GigabitEthernet4 no ip address ! interface GigabitEthernet5 no ip address ! interface GigabitEthernet6 no ip address ! interface GigabitEthernet7 switchport access vlan 99 no ip address ! interface GigabitEthernet8 ip address 172.16.0.2 255.255.255.0 duplex auto speed auto ! interface Vlan1 no ip address ! interface Vlan10 ip address 10.0.0.2 255.255.255.0 ! interface Vlan99 ip address 192.168.99.4 255.255.255.0 ! interface Async3 no ip address encapsulation slip ! ip forward-protocol nd no ip http server no ip http secure-server ! ! ip route 172.16.1.0 255.255.255.0 10.10.2.3 ! ! ! control-plane ! ! mgcp behavior rsip-range tgcp-only mgcp behavior comedia-role none mgcp behavior comedia-check-media-src disable mgcp behavior comedia-sdp-force disable ! mgcp profile default ! ! ! ! ! ! ! line con 0 login local no modem enable line aux 0 line 3 modem InOut speed 115200 flowcontrol hardware line vty 0 4 login local transport input all ! scheduler allocate 20000 1000 ! ! ! end |
RT03# sh run
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 |
RT03#sh run Building configuration... Current configuration : 2059 bytes ! ! Last configuration change at 01:13:00 UTC Tue Jan 28 2025 by admin ! version 15.4 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname RT03 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$io5s$H45.fHTZi4WsynedlDusr1 ! no aaa new-model ! ! ! ! ! ! ! ! ! ! ! ! ! ! no ip domain lookup ip domain name orange.local ip cef no ipv6 cef ! ! ! ! ! multilink bundle-name authenticated ! ! ! ! ! ! ! ! cts logging verbose license udi pid C891FJ-K9 sn FGL2333210N ! ! vtp mode transparent username admin password 7 070E25414707 ! ! ! ! ! vlan 10,99 ! ! ! ! ! ! ! ! ! ! ! ! interface BRI0 no ip address encapsulation hdlc shutdown isdn termination multidrop ! interface FastEthernet0 ip address 10.10.2.3 255.255.255.0 duplex auto speed auto ! interface GigabitEthernet0 switchport access vlan 10 no ip address ! interface GigabitEthernet1 no ip address ! interface GigabitEthernet2 no ip address ! interface GigabitEthernet3 no ip address ! interface GigabitEthernet4 no ip address ! interface GigabitEthernet5 no ip address ! interface GigabitEthernet6 no ip address ! interface GigabitEthernet7 switchport access vlan 99 no ip address ! interface GigabitEthernet8 ip address 172.16.1.3 255.255.255.0 duplex auto speed auto ! interface Vlan1 no ip address ! interface Vlan10 ip address 10.0.1.3 255.255.255.0 ! interface Vlan99 ip address 192.168.99.5 255.255.255.0 ! interface Async3 no ip address encapsulation slip ! ip forward-protocol nd no ip http server no ip http secure-server ! ! ip route 172.16.0.0 255.255.255.0 10.10.2.2 ip ssh version 2 ! ! ! control-plane ! ! mgcp behavior rsip-range tgcp-only mgcp behavior comedia-role none mgcp behavior comedia-check-media-src disable mgcp behavior comedia-sdp-force disable ! mgcp profile default ! ! ! ! ! ! ! line con 0 login local no modem enable line aux 0 line 3 modem InOut speed 115200 flowcontrol hardware line vty 0 4 login local transport input all ! scheduler allocate 20000 1000 ! ! ! end |
RT04# sh run
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 |
RT04#sh run Building configuration... Current configuration : 2680 bytes ! ! Last configuration change at 04:47:31 UTC Tue Jan 28 2025 by admin ! version 15.4 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname RT04 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$bAlC$CYqdi73zMml1PZfAOldV1/ ! no aaa new-model memory-size iomem 15 ! ! ! ! ! ! ! ! ! ! ! ! ! ! no ip domain lookup ip domain name orange.local ip cef no ipv6 cef ! ! ! ! ! multilink bundle-name authenticated ! ! ! ! ! ! ! ! cts logging verbose license udi pid C891FJ-K9 sn FGL2505LDKP ! ! vtp mode transparent username admin password 7 020700560208 ! ! ! ! ! vlan 99 ! ip ssh version 2 ! ! crypto isakmp policy 1 encr 3des hash md5 authentication pre-share group 2 crypto isakmp key orange address 172.16.0.1 crypto isakmp keepalive 10 periodic ! ! crypto ipsec transform-set ORANGE-IPSEC esp-3des esp-md5-hmac mode transport ! ! ! crypto map Cryoto-ipsec-map 1 ipsec-isakmp set peer 172.16.0.1 set transform-set ORANGE-IPSEC match address Allow-ipsec-p2p ! ! ! ! ! ! interface Tunnel0 ip address 192.168.1.2 255.255.255.0 ip mtu 1372 tunnel source GigabitEthernet8 tunnel destination 172.16.0.1 ! interface BRI0 no ip address encapsulation hdlc shutdown isdn termination multidrop ! interface FastEthernet0 ip address 10.0.1.4 255.255.255.0 ip tcp adjust-mss 1332 duplex auto speed auto ! interface GigabitEthernet0 no ip address ! interface GigabitEthernet1 no ip address ! interface GigabitEthernet2 no ip address ! interface GigabitEthernet3 no ip address ! interface GigabitEthernet4 no ip address ! interface GigabitEthernet5 no ip address ! interface GigabitEthernet6 no ip address ! interface GigabitEthernet7 switchport access vlan 99 no ip address ! interface GigabitEthernet8 ip address 172.16.1.4 255.255.255.0 duplex auto speed auto crypto map Cryoto-ipsec-map ! interface Vlan1 no ip address ! interface Vlan99 ip address 192.168.99.6 255.255.255.0 ! interface Async3 no ip address encapsulation slip ! ip forward-protocol nd no ip http server no ip http secure-server ! ! ip route 0.0.0.0 0.0.0.0 Tunnel0 ip route 172.16.0.1 255.255.255.255 172.16.1.3 ! ip access-list extended Allow-ipsec-p2p permit gre host 172.16.1.4 host 172.16.0.1 ! ! ! control-plane ! ! mgcp behavior rsip-range tgcp-only mgcp behavior comedia-role none mgcp behavior comedia-check-media-src disable mgcp behavior comedia-sdp-force disable ! mgcp profile default ! ! ! ! ! ! ! line con 0 login local no modem enable line aux 0 line 3 modem InOut speed 115200 flowcontrol hardware line vty 0 4 login local transport input all ! scheduler allocate 20000 1000 ! ! ! end |
設定とパケットについて
ルーティングについて
当たり前ですが、RT02とRT03にはRT01とRT04が持つセグメントを持っていますが、トンネリングされているので問題なくRT01からRT04への通信が行うことができます。トンネリングされていないと、RT02やRT03が持つセグメントでIP重複が発生する可能性がありますので、トンネリングの効用についても一緒に確認しています。
暗号化の対象に注目する
紹介しているconfigを環境に合わせてIPを変更すればあまり考えずに使えますが、設定項目について少しだけ補足。
RT01内の「ip access-list extended Allow-ipsec-p2p」の「permit gre host 172.16.0.1 host 172.16.1.4」の部分。GREを使わないでIPsecだけを使う場合と比較すると、通信処理の部分の理解にもつながります。
IPsec単体の場合、この部分の指定は「permit ip 10.0.0.0 0.0.0.255 10.10.1.0 0.0.0.255」になります。このパラメータでIPsecで転送するパケットの範囲を指定します。10.0.0.0/24から10.0.1.0/24宛の通信があった場合、IPsecで暗号化するという意味になります。
では、今回の「permit gre host 172.16.0.1 host 172.16.1.4」はどうなるか。GREトンネルの通信が発生した場合IPsecの暗号化を行うこと言うことになります。つまり、通信処理の順序は
①ルーティングテーブルを確認
②トンネルインターフェースがネクストホップ
③GREのトンネリング
④IPsecの暗号化
となるわけです。GREのルーティング対象になるパケットはすべてIPsec暗号化してくれるので、configとしてすっきりするわけです。1行で収まってしまう分存在感がないので、注目してみました。
暗号化時のパケット
PC01からPC04にICMP(Ping)を行います。
IPSecによって暗号化されているので、ICMP自体の通信は見えません。(所々ISAKMPが挟まっています)
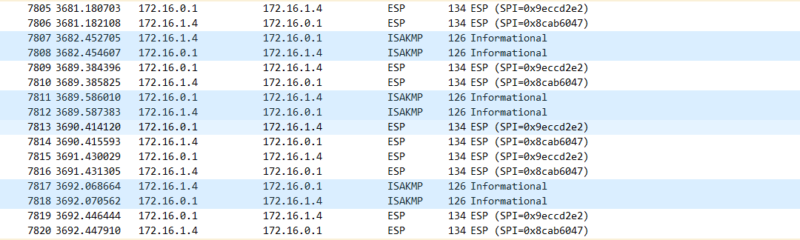
ステータス確認
コマンド:sh crypt isakmap sa
stateが「QM_Idle」になっていると、IKEフェーズ1の成功していることを示しています。このステータスが「-」や「MM_NO_STATE」の場合、IPsec通信の設定を見直しや構成しているルータの設定、途中経路の疎通を確認する必要があります。
実行結果
|
1 2 3 4 5 6 |
RT01#sh crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 172.16.1.4 172.16.0.1 QM_IDLE 2001 ACTIVE IPv6 Crypto ISAKMP SA |
コマンド:sh crypt isakmap sa
注目するところは「 #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4」「#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4」の部分。IPsec通信が発生した分だけカウンタが上がるので、このカウンタが上がらない場合はIPsecの通信ができていないことになります。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
RT01#sh crypto ipsec sa interface: GigabitEthernet8 Crypto map tag: Crypto-ipsec-map, local addr 172.16.0.1 protected vrf: (none) local ident (addr/mask/prot/port): (172.16.0.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (172.16.1.4/255.255.255.255/47/0) current_peer 172.16.1.4 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.16.0.1, remote crypto endpt.: 172.16.1.4 plaintext mtu 1466, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet8 current outbound spi: 0x9ECCD2E2(2664223458) PFS (Y/N): N, DH group: none inbound esp sas: spi: 0x8CAB6047(2360041543) transform: esp-3des esp-md5-hmac , in use settings ={Transport, } conn id: 1, flow_id: Onboard VPN:1, sibling_flags 80004000, crypto map: Crypto-ipsec-map sa timing: remaining key lifetime (k/sec): (4170458/3476) IV size: 8 bytes replay detection support: Y Status: ACTIVE(ACTIVE) inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0x9ECCD2E2(2664223458) transform: esp-3des esp-md5-hmac , in use settings ={Transport, } conn id: 2, flow_id: Onboard VPN:2, sibling_flags 80004000, crypto map: Crypto-ipsec-map sa timing: remaining key lifetime (k/sec): (4170458/3476) IV size: 8 bytes replay detection support: Y Status: ACTIVE(ACTIVE) outbound ah sas: outbound pcp sas: |
IPsecを無効にしたときのパケット
一度IPsecを無効にしてみます。(RT04でも同じコマンドを実行)
|
1 2 3 4 5 |
RT01#conf t Enter configuration commands, one per line. End with CNTL/Z. RT01(config)#int gigabitEthernet 8 RT01(config-if)#no crypto map Crypto-ipsec-map RT01(config-if)#end |
isamkp、ipsecのステータスは下記の通り。
|
1 2 3 4 5 6 7 8 9 |
RT01#sh crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 172.16.1.4 172.16.0.1 MM_NO_STATE 2001 ACTIVE (deleted) IPv6 Crypto ISAKMP SA RT01#sh crypto ipsec sa No SAs found |
PC01からPingを実行し、その時のRT02とRT03間の通信を見てみます。先ほどとの違いは明確で、ICMPの通信がそのまま見えます。一見GREトンネルもされていなさそうですが、172.16.0.1から172.16.1.14宛のパケットでちゃんとカプセリングされています。
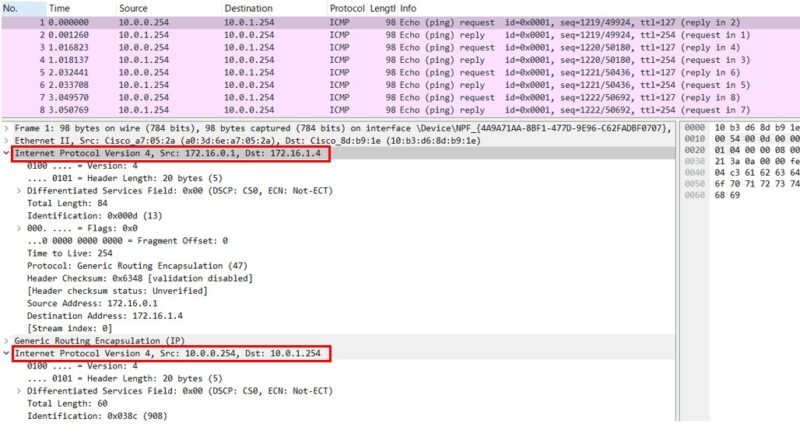
うまくいかないときはdebugを有効にする
下記コマンドでdebugを有効にしておきます。logはけっこうな量が出力されるので、logの保存容量も相応に大きくしておきます。
|
1 2 3 |
debug crypt isakmp debug crypt ipsec logging buffered 512000 |
IPsec成功ログ
検証時は失敗する中で突如成功して、どこから成功のログ?という感じになることが多かったので、成功時に出力されるログを記録として残しておきます。少し長いですが。
RT01 # sh log
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 |
RT01#sh logging Syslog logging: enabled (0 messages dropped, 3 messages rate-limited, 0 flushes, 0 overruns, xml disabled, filtering disabled) No Active Message Discriminator. No Inactive Message Discriminator. Console logging: level debugging, 295 messages logged, xml disabled, filtering disabled Monitor logging: level debugging, 0 messages logged, xml disabled, filtering disabled Buffer logging: level debugging, 250 messages logged, xml disabled, filtering disabled Exception Logging: size (8192 bytes) Count and timestamp logging messages: disabled Persistent logging: disabled No active filter modules. Trap logging: level informational, 51 message lines logged Logging Source-Interface: VRF Name: Log Buffer (51200 bytes): *Mar 18 14:20:24.303: %SYS-5-LOG_CONFIG_CHANGE: Buffer logging: level debugging, xml disabled, filtering disabled, size (51200) *Mar 18 14:20:24.983: %SYS-5-CONFIG_I: Configured from console by admin on vty0 (192.168.99.252) *Mar 18 14:21:04.655: IPSEC(sa_request): , (key eng. msg.) OUTBOUND local= 172.16.0.1:500, remote= 172.16.1.4:500, local_proxy= 172.16.0.1/255.255.255.255/47/0, remote_proxy= 172.16.1.4/255.255.255.255/47/0, protocol= ESP, transform= esp-3des esp-md5-hmac (Transport), lifedur= 3600s and 4608000kb, spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0 *Mar 18 14:21:04.655: ISAKMP:(0): SA request profile is (NULL) *Mar 18 14:21:04.659: ISAKMP: Created a peer struct for 172.16.1.4, peer port 500 *Mar 18 14:21:04.659: ISAKMP: New peer created peer = 0x361D584 peer_handle = 0x80000002 *Mar 18 14:21:04.659: ISAKMP: Locking peer struct 0x361D584, refcount 1 for isakmp_initiator *Mar 18 14:21:04.659: ISAKMP: local port 500, remote port 500 *Mar 18 14:21:04.659: ISAKMP: set new node 0 to QM_IDLE *Mar 18 14:21:04.659: ISAKMP:(0):insert sa successfully sa = 2B8128C *Mar 18 14:21:04.659: ISAKMP:(0):Can not start Aggressive mode, trying Main mode. *Mar 18 14:21:04.659: ISAKMP:(0):found peer pre-shared key matching 172.16.1.4 *Mar 18 14:21:04.659: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID *Mar 18 14:21:04.659: ISAKMP:(0): constructed NAT-T vendor-07 ID *Mar 18 14:21:04.659: ISAKMP:(0): constructed NAT-T vendor-03 ID *Mar 18 14:21:04.659: ISAKMP:(0): constructed NAT-T vendor-02 ID *Mar 18 14:21:04.659: ISAKMP:(0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM *Mar 18 14:21:04.659: ISAKMP:(0):Old State = IKE_READY New State = IKE_I_MM1 *Mar 18 14:21:04.659: ISAKMP:(0): beginning Main Mode exchange *Mar 18 14:21:04.659: ISAKMP:(0): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) MM_NO_STATE *Mar 18 14:21:04.659: ISAKMP:(0):Sending an IKE IPv4 Packet. *Mar 18 14:21:04.663: ISAKMP (0): received packet from 172.16.1.4 dport 500 sport 500 Global (I) MM_NO_STATE *Mar 18 14:21:04.663: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH *Mar 18 14:21:04.663: ISAKMP:(0):Old State = IKE_I_MM1 New State = IKE_I_MM2 *Mar 18 14:21:04.663: ISAKMP:(0): processing SA payload. message ID = 0 *Mar 18 14:21:04.663: ISAKMP:(0): processing vendor id payload *Mar 18 14:21:04.663: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch *Mar 18 14:21:04.663: ISAKMP (0): vendor ID is NAT-T RFC 3947 *Mar 18 14:21:04.663: ISAKMP:(0):found peer pre-shared key matching 172.16.1.4 *Mar 18 14:21:04.663: ISAKMP:(0): local preshared key found *Mar 18 14:21:04.663: ISAKMP : Scanning profiles for xauth ... *Mar 18 14:21:04.663: ISAKMP:(0):Checking ISAKMP transform 1 against priority 1 policy *Mar 18 14:21:04.663: ISAKMP: encryption 3DES-CBC *Mar 18 14:21:04.663: ISAKMP: hash MD5 *Mar 18 14:21:04.663: ISAKMP: default group 2 *Mar 18 14:21:04.663: ISAKMP: auth pre-share *Mar 18 14:21:04.663: ISAKMP: life type in seconds *Mar 18 14:21:04.663: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80 *Mar 18 14:21:04.663: ISAKMP:(0):atts are acceptable. Next payload is 0 *Mar 18 14:21:04.663: ISAKMP:(0):Acceptable atts:actual life: 0 *Mar 18 14:21:04.663: ISAKMP:(0):Acceptable atts:life: 0 *Mar 18 14:21:04.663: ISAKMP:(0):Fill atts in sa vpi_length:4 *Mar 18 14:21:04.663: ISAKMP:(0):Fill atts in sa life_in_seconds:86400 *Mar 18 14:21:04.663: ISAKMP:(0):Returning Actual lifetime: 86400 *Mar 18 14:21:04.663: ISAKMP:(0)::Started lifetime timer: 86400. *Mar 18 14:21:04.663: ISAKMP:(0): processing vendor id payload *Mar 18 14:21:04.663: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch *Mar 18 14:21:04.663: ISAKMP (0): vendor ID is NAT-T RFC 3947 *Mar 18 14:21:04.663: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE *Mar 18 14:21:04.663: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM2 *Mar 18 14:21:04.663: ISAKMP:(0): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) MM_SA_SETUP *Mar 18 14:21:04.663: ISAKMP:(0):Sending an IKE IPv4 Packet. *Mar 18 14:21:04.663: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE *Mar 18 14:21:04.663: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM3 *Mar 18 14:21:04.667: ISAKMP (0): received packet from 172.16.1.4 dport 500 sport 500 Global (I) MM_SA_SETUP *Mar 18 14:21:04.667: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH *Mar 18 14:21:04.667: ISAKMP:(0):Old State = IKE_I_MM3 New State = IKE_I_MM4 *Mar 18 14:21:04.667: ISAKMP:(0): processing KE payload. message ID = 0 *Mar 18 14:21:04.671: ISAKMP:(0): processing NONCE payload. message ID = 0 *Mar 18 14:21:04.671: ISAKMP:(0):found peer pre-shared key matching 172.16.1.4 *Mar 18 14:21:04.671: ISAKMP:(2001): processing vendor id payload *Mar 18 14:21:04.671: ISAKMP:(2001): vendor ID is Unity *Mar 18 14:21:04.671: ISAKMP:(2001): processing vendor id payload *Mar 18 14:21:04.671: ISAKMP:(2001): vendor ID is DPD *Mar 18 14:21:04.671: ISAKMP:(2001): processing vendor id payload *Mar 18 14:21:04.671: ISAKMP:(2001): speaking to another IOS box! *Mar 18 14:21:04.671: ISAKMP:received payload type 20 *Mar 18 14:21:04.671: ISAKMP (2001): His hash no match - this node outside NAT *Mar 18 14:21:04.671: ISAKMP:received payload type 20 *Mar 18 14:21:04.671: ISAKMP (2001): No NAT Found for self or peer *Mar 18 14:21:04.671: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE *Mar 18 14:21:04.671: ISAKMP:(2001):Old State = IKE_I_MM4 New State = IKE_I_MM4 *Mar 18 14:21:04.671: ISAKMP:(2001):Send initial contact *Mar 18 14:21:04.671: ISAKMP:(2001):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR *Mar 18 14:21:04.671: ISAKMP (2001): ID payload next-payload : 8 type : 1 address : 172.16.0.1 protocol : 17 port : 500 length : 12 *Mar 18 14:21:04.671: ISAKMP:(2001):Total payload length: 12 *Mar 18 14:21:04.671: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) MM_KEY_EXCH *Mar 18 14:21:04.671: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:04.671: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE *Mar 18 14:21:04.671: ISAKMP:(2001):Old State = IKE_I_MM4 New State = IKE_I_MM5 *Mar 18 14:21:04.675: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) MM_KEY_EXCH *Mar 18 14:21:04.675: ISAKMP:(2001): processing ID payload. message ID = 0 *Mar 18 14:21:04.675: ISAKMP (2001): ID payload next-payload : 8 type : 1 address : 172.16.1.4 protocol : 17 port : 500 length : 12 *Mar 18 14:21:04.675: ISAKMP:(0):: peer matches *none* of the profiles *Mar 18 14:21:04.675: ISAKMP:(2001): processing HASH payload. message ID = 0 *Mar 18 14:21:04.675: ISAKMP:(2001):SA authentication status: authenticated *Mar 18 14:21:04.675: ISAKMP:(2001):SA has been authenticated with 172.16.1.4 *Mar 18 14:21:04.675: ISAKMP: Trying to insert a peer 172.16.0.1/172.16.1.4/500/, and inserted successfully 361D584. *Mar 18 14:21:04.675: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH *Mar 18 14:21:04.675: ISAKMP:(2001):Old State = IKE_I_MM5 New State = IKE_I_MM6 *Mar 18 14:21:04.675: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE *Mar 18 14:21:04.675: ISAKMP:(2001):Old State = IKE_I_MM6 New State = IKE_I_MM6 *Mar 18 14:21:04.675: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE *Mar 18 14:21:04.675: ISAKMP:(2001):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE *Mar 18 14:21:04.675: ISAKMP:(2001):IKE_DPD is enabled, initializing timers *Mar 18 14:21:04.675: ISAKMP:(2001):beginning Quick Mode exchange, M-ID of 332082047 *Mar 18 14:21:04.675: ISAKMP:(2001):QM Initiator gets spi *Mar 18 14:21:04.675: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:04.675: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:04.675: ISAKMP:(2001):Node 332082047, Input = IKE_MESG_INTERNAL, IKE_INIT_QM *Mar 18 14:21:04.675: ISAKMP:(2001):Old State = IKE_QM_READY New State = IKE_QM_I_QM1 *Mar 18 14:21:04.675: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE *Mar 18 14:21:04.675: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:04.679: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) QM_IDLE *Mar 18 14:21:04.679: ISAKMP:(2001): processing HASH payload. message ID = 332082047 *Mar 18 14:21:04.679: ISAKMP:(2001): processing SA payload. message ID = 332082047 *Mar 18 14:21:04.679: ISAKMP:(2001):Checking IPSec proposal 1 *Mar 18 14:21:04.679: ISAKMP: transform 1, ESP_3DES *Mar 18 14:21:04.679: ISAKMP: attributes in transform: *Mar 18 14:21:04.679: ISAKMP: encaps is 2 (Transport) *Mar 18 14:21:04.679: ISAKMP: SA life type in seconds *Mar 18 14:21:04.679: ISAKMP: SA life duration (basic) of 3600 *Mar 18 14:21:04.679: ISAKMP: SA life type in kilobytes *Mar 18 14:21:04.679: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0 *Mar 18 14:21:04.679: ISAKMP: authenticator is HMAC-MD5 *Mar 18 14:21:04.679: ISAKMP:(2001):atts are acceptable. *Mar 18 14:21:04.679: IPSEC(validate_proposal_request): proposal part #1 *Mar 18 14:21:04.679: IPSEC(validate_proposal_request): proposal part #1, (key eng. msg.) INBOUND local= 172.16.0.1:0, remote= 172.16.1.4:0, local_proxy= 172.16.0.1/255.255.255.255/47/0, remote_proxy= 172.16.1.4/255.255.255.255/47/0, protocol= ESP, transform= esp-3des esp-md5-hmac (Transport), lifedur= 0s and 0kb, spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0 *Mar 18 14:21:04.679: Crypto mapdb : proxy_match src addr : 172.16.0.1 dst addr : 172.16.1.4 protocol : 47 src port : 0 dst port : 0 *Mar 18 14:21:04.679: (ipsec_process_proposal)Map Accepted: Crypto-ipsec-map, 1 *Mar 18 14:21:04.679: ISAKMP:(2001): processing NONCE payload. message ID = 332082047 *Mar 18 14:21:04.679: ISAKMP:(2001): processing ID payload. message ID = 332082047 *Mar 18 14:21:04.679: ISAKMP:(2001): processing ID payload. message ID = 332082047 *Mar 18 14:21:04.683: ISAKMP:(2001):Node 332082047, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH *Mar 18 14:21:04.683: ISAKMP:(2001):Old State = IKE_QM_I_QM1 New State = IKE_QM_IPSEC_INSTALL_AWAIT *Mar 18 14:21:04.683: IPSEC(key_engine): got a queue event with 1 KMI message(s) *Mar 18 14:21:04.683: Crypto mapdb : proxy_match src addr : 172.16.0.1 dst addr : 172.16.1.4 protocol : 47 src port : 0 dst port : 0 *Mar 18 14:21:04.683: IPSEC(crypto_ipsec_create_ipsec_sas): Map found Crypto-ipsec-map, 1 *Mar 18 14:21:04.683: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer 172.16.1.4 *Mar 18 14:21:04.683: IPSEC(create_sa): sa created, (sa) sa_dest= 172.16.0.1, sa_proto= 50, sa_spi= 0x8CAB6047(2360041543), sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 1 sa_lifetime(k/sec)= (4608000/3600), (identity) local= 172.16.0.1:0, remote= 172.16.1.4:0, local_proxy= 172.16.0.1/255.255.255.255/47/0, remote_proxy= 172.16.1.4/255.255.255.255/47/0 *Mar 18 14:21:04.683: IPSEC(create_sa): sa created, (sa) sa_dest= 172.16.1.4, sa_proto= 50, sa_spi= 0x9ECCD2E2(2664223458), sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2 sa_lifetime(k/sec)= (4608000/3600), (identity) local= 172.16.0.1:0, remote= 172.16.1.4:0, local_proxy= 172.16.0.1/255.255.255.255/47/0, remote_proxy= 172.16.1.4/255.255.255.255/47/0 *Mar 18 14:21:04.683: IPSEC: Expand action denied, notify RP *Mar 18 14:21:04.683: ISAKMP: Failed to find peer index node to update peer_info_list *Mar 18 14:21:04.683: ISAKMP:(2001):Received IPSec Install callback... proceeding with the negotiation *Mar 18 14:21:04.683: ISAKMP:(2001):Successfully installed IPSEC SA (SPI:0x8CAB6047) on GigabitEthernet8 *Mar 18 14:21:04.683: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:04.683: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:04.683: ISAKMP:(2001):deleting node 332082047 error FALSE reason "No Error" *Mar 18 14:21:04.683: ISAKMP:(2001):Node 332082047, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE *Mar 18 14:21:04.683: ISAKMP:(2001):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_PHASE2_COMPLETE *Mar 18 14:21:14.675: ISAKMP: set new node 1259728541 to QM_IDLE *Mar 18 14:21:14.675: ISAKMP:(2001):Sending NOTIFY DPD/R_U_THERE protocol 1 spi 54704528, message ID = 1259728541 *Mar 18 14:21:14.675: ISAKMP:(2001): seq. no 0x63071F96 *Mar 18 14:21:14.675: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:14.675: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:14.675: ISAKMP:(2001):purging node 1259728541 *Mar 18 14:21:14.675: ISAKMP:(2001):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_IM_ALIVE *Mar 18 14:21:14.675: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:14.675: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) QM_IDLE *Mar 18 14:21:14.675: ISAKMP: set new node 1588210084 to QM_IDLE *Mar 18 14:21:14.675: ISAKMP:(2001): processing HASH payload. message ID = 1588210084 *Mar 18 14:21:14.675: ISAKMP:(2001): processing NOTIFY DPD/R_U_THERE protocol 1 spi 0, message ID = 1588210084, sa = 0x2B8128C *Mar 18 14:21:14.675: ISAKMP:(2001):deleting node 1588210084 error FALSE reason "Informational (in) state 1" *Mar 18 14:21:14.675: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Mar 18 14:21:14.675: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:14.675: ISAKMP:(2001):DPD/R_U_THERE received from peer 172.16.1.4, sequence 0x33508612 *Mar 18 14:21:14.675: ISAKMP: set new node -477532072 to QM_IDLE *Mar 18 14:21:14.675: ISAKMP:(2001):Sending NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 54704456, message ID = 3817435224 *Mar 18 14:21:14.675: ISAKMP:(2001): seq. no 0x33508612 *Mar 18 14:21:14.675: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:14.675: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:14.675: ISAKMP:(2001):purging node -477532072 *Mar 18 14:21:14.675: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_MESG_KEEP_ALIVE *Mar 18 14:21:14.675: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:14.675: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) QM_IDLE *Mar 18 14:21:14.675: ISAKMP: set new node 1680226564 to QM_IDLE *Mar 18 14:21:14.675: ISAKMP:(2001): processing HASH payload. message ID = 1680226564 *Mar 18 14:21:14.675: ISAKMP:(2001): processing NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 0, message ID = 1680226564, sa = 0x2B8128C *Mar 18 14:21:14.675: ISAKMP:(2001): DPD/R_U_THERE_ACK received from peer 172.16.1.4, sequence 0x63071F96 *Mar 18 14:21:14.675: ISAKMP:(2001):deleting node 1680226564 error FALSE reason "Informational (in) state 1" *Mar 18 14:21:14.675: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Mar 18 14:21:14.675: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:17.155: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) QM_IDLE *Mar 18 14:21:17.155: ISAKMP: set new node -1091190389 to QM_IDLE *Mar 18 14:21:17.155: ISAKMP:(2001): processing HASH payload. message ID = 3203776907 *Mar 18 14:21:17.155: ISAKMP:(2001): processing NOTIFY DPD/R_U_THERE protocol 1 spi 0, message ID = 3203776907, sa = 0x2B8128C *Mar 18 14:21:17.155: ISAKMP:(2001):deleting node -1091190389 error FALSE reason "Informational (in) state 1" *Mar 18 14:21:17.155: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Mar 18 14:21:17.155: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:17.155: ISAKMP:(2001):DPD/R_U_THERE received from peer 172.16.1.4, sequence 0x33508613 *Mar 18 14:21:17.155: ISAKMP: set new node 705161519 to QM_IDLE *Mar 18 14:21:17.155: ISAKMP:(2001):Sending NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 54704456, message ID = 705161519 *Mar 18 14:21:17.155: ISAKMP:(2001): seq. no 0x33508613 *Mar 18 14:21:17.155: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:17.155: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:17.155: ISAKMP:(2001):purging node 705161519 *Mar 18 14:21:17.155: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_MESG_KEEP_ALIVE *Mar 18 14:21:17.155: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:24.563: ISAKMP: set new node 1225461111 to QM_IDLE *Mar 18 14:21:24.563: ISAKMP:(2001):Sending NOTIFY DPD/R_U_THERE protocol 1 spi 54704528, message ID = 1225461111 *Mar 18 14:21:24.563: ISAKMP:(2001): seq. no 0x63071F97 *Mar 18 14:21:24.563: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:24.563: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:24.563: ISAKMP:(2001):purging node 1225461111 *Mar 18 14:21:24.563: ISAKMP:(2001):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_IM_ALIVE *Mar 18 14:21:24.563: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:24.563: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) QM_IDLE *Mar 18 14:21:24.563: ISAKMP: set new node -393489513 to QM_IDLE *Mar 18 14:21:24.563: ISAKMP:(2001): processing HASH payload. message ID = 3901477783 *Mar 18 14:21:24.563: ISAKMP:(2001): processing NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 0, message ID = 3901477783, sa = 0x2B8128C *Mar 18 14:21:24.563: ISAKMP:(2001): DPD/R_U_THERE_ACK received from peer 172.16.1.4, sequence 0x63071F97 *Mar 18 14:21:24.563: ISAKMP:(2001):deleting node -393489513 error FALSE reason "Informational (in) state 1" *Mar 18 14:21:24.563: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Mar 18 14:21:24.563: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:27.123: ISAKMP (2001): received packet from 172.16.1.4 dport 500 sport 500 Global (I) QM_IDLE *Mar 18 14:21:27.123: ISAKMP: set new node 1011759196 to QM_IDLE *Mar 18 14:21:27.123: ISAKMP:(2001): processing HASH payload. message ID = 1011759196 *Mar 18 14:21:27.123: ISAKMP:(2001): processing NOTIFY DPD/R_U_THERE protocol 1 spi 0, message ID = 1011759196, sa = 0x2B8128C *Mar 18 14:21:27.123: ISAKMP:(2001):deleting node 1011759196 error FALSE reason "Informational (in) state 1" *Mar 18 14:21:27.123: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Mar 18 14:21:27.123: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Mar 18 14:21:27.123: ISAKMP:(2001):DPD/R_U_THERE received from peer 172.16.1.4, sequence 0x33508614 *Mar 18 14:21:27.123: ISAKMP: set new node 142360442 to QM_IDLE *Mar 18 14:21:27.123: ISAKMP:(2001):Sending NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 54704456, message ID = 142360442 *Mar 18 14:21:27.123: ISAKMP:(2001): seq. no 0x33508614 *Mar 18 14:21:27.123: ISAKMP:(2001): sending packet to 172.16.1.4 my_port 500 peer_port 500 (I) QM_IDLE *Mar 18 14:21:27.123: ISAKMP:(2001):Sending an IKE IPv4 Packet. *Mar 18 14:21:27.123: ISAKMP:(2001):purging node 142360442 *Mar 18 14:21:27.123: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_MESG_KEEP_ALIVE *Mar 18 14:21:27.123: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE |
解除を忘れずに。下記で解除できます。
|
1 |
undebug all |

